Digital Security Awareness
Keeping the Oneida Nation informed and safe, one click at a time.
Welcome

Here are our 10 top tips to stay safe online:
1. KEEP A CLEAN MACHINE
Keep all software on internet connected devices – including personal computers, smartphones and tablets – current to reduce risk of infection from ransomware and malware. If you want to “set it and forget it,” configure your devices to automatically update or to notify you when an update is available.
2. CREATE LONG, UNIQUE PASSWORDS
Length trumps complexity. Strong passwords are at least 12 characters long and include letters, numbers and symbols. Ideally, your password is not recognizable as a word or phrase. And, yes, you should have a unique password for each online account. Sounds hard to remember? Using a password manager has never been easier (we’ll say more in a second) – many smartphones and web browsers include password managers and even suggest strong passwords. Otherwise, we recommend coming up with a password that is actually a “passphrase,” that is, a sentence that is at least 12 characters long. Focus on positive sentences or phrases that you like to think about and are easy to remember, such as ILov3StayingSafeOnl1ne! (but don’t use that one).
3. USE A PASSWORD MANAGER
It’s time to ditch the notebook if that’s where you keep your passwords – use it for doodles. Ditto for that Notes app or word processing doc – save the hard drive space. Instead, the simplest, most secure way to manage unique passwords is through a password manager application. A password manager is software created to manage all your online credentials like usernames and passwords. Many are free. Often, browsers and device operating systems include password management programs. Password managers store your passwords in an encrypted database (think of it as your personal data vault). These programs also generate new passwords when you need them. Really, it has never been easier to safely generate, store and access your passwords. (Please see ‘Recommended Downloads’ section).
4. ENABLE MULTI-FACTOR AUTHENTICATION
Multi-factor authentication (MFA), sometimes called 2-factor authentication, adds a whole other level of security to your key accounts. MFA includes biometrics (think face ID scans or fingerprint access), security keys or apps that send you unique, one-time codes when you want to log on to a sensitive account. We recommend you use MFA whenever offered. Read more about the different types of MFA.
5. THINK BEFORE YOU CLICK
What’s the most common way for cybercriminals to get your sensitive information? It’s when you click on something you shouldn’t have. Malicious links in email, tweets, texts, posts, social media messages and malicious online advertising (known as malvertising) are a direct way for hackers to get your sensitive information. Don’t make it easy for them. Be wary of clicking on links or downloading anything that comes from a stranger or that you were not expecting. Whenever you get an email or message, count to five – usually that’s all the time you need to determine if the missive seems authentic or not.
6. REPORT PHISHING
One of the best ways to take down cybercriminals is by reporting phishing attempts, and nowadays its easier than ever. If the email came to your work email address, report it to your IT manager or security team as quickly as possible. If you’re at home and the email came to your personal email address, do not click on any links (even the unsubscribe link) or reply back to the email. Most email programs and social media platforms allow you to report phishing attempts. But don’t keep that phishing message around – delete it ASAP. You can further protect yourself by blocking the sender from your email program, social media platform or phone.
7. USE SECURE WI-FI
Public wireless networks and hotspots are unsecured, which means that anyone could potentially see what you are doing on your laptop or smartphone while you are connected to them. Limit what you do on public WiFi. Especially avoid logging in to key accounts like email and financial services. Consider using a virtual private network (VPN) or a personal/mobile hotspot if you need a more secure connection.
8. BACK IT UP
The best way to protect your valuable work, music, photos, data and other digital information is to make copies and store them safely. If you have a copy of your data and your device falls victim to ransomware or other cyber threats, you will be able to restore the data from a backup. If you break your computer or it crashes, you won’t lose the data along with the device. Use the 3-2-1 rule as a guide to backing up your data. The rule is: keep at least three (3) copies of your data, and store two (2) backup copies on different storage media, with one (1) of them located offsite. One of these storage possibilities can be backing up to the cloud, which are secure computer servers you can access through an account.
9. CHECK YOUR SETTINGS
Every time you sign up for a new account, download a new app or get a new device, immediately configure the privacy and security settings to your comfort level for information sharing. Regularly check these settings to make sure they are still configured to your comfort. Audit your apps, platforms and games every few months and delete ones you no longer use – then you don’t need to check their settings!
10. SHARE WITH CARE
Think before posting about yourself and others online. Consider what a post reveals, who might see it and how it might affect you or others.
List provided by:
*!?*Oneida Casino Hotel Facebook Scam Alert*?!*
We want to make you aware of a scam currently circulating on Facebook and Instagram involving fake ads that falsely claim to represent Oneida Casino Hotel.
These counterfeit ads are promoting online gambling under our name and offering false rewards like a $1,000 welcome bonus and 150 free spins. They then attempt to collect personal and financial information from users.
• These ads and the page they link to are fraudulent.
• Oneida Casino Hotel does NOT operate any online gaming or promotional giveaways through Facebook ads.
What to Watch For:
If you see one of these ads, please report it directly to Meta as scam by clicking on the three small dots on the top right of the ads. (Regrettably, there is no phone number to report this fraud—reporting via the interface is our only option.)
Example of the fraudulent ad:
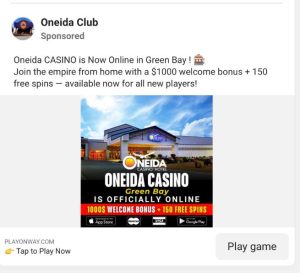
Fake Facebook page posing as Oneida Casino Hotel:
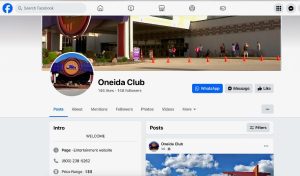
Stay Safe:
• Do not click on any suspicious ads claiming to be from Oneida Casino Hotel.
• Never provide your personal or financial details through third-party links.
• Always verify information through our official website or call us directly.
Official Website:
oneidacasinohotel.com
Official Contact Numbers:
Casino: 1.800.238.4263, 920.494.4500
Hotel: 1.800.238.4263, 920.494.7300
Already Interacted with a Scam Ad?
If you believe you may have been scammed, please take the following steps immediately:
1. Report the Incident:
• Internet Crime Complaint Center (IC3): Visit www.ic3.gov to file a complaint. The IC3 is run by the FBI and serves as the central hub for reporting cyber-enabled crimes.
• Federal Trade Commission (FTC): Report the scam at ReportFraud.ftc.gov. The FTC investigates fraud, scams, and deceptive business practices.
2. Contact Your Bank
If you shared financial information or notice unauthorized transactions, call your bank immediately to freeze your account, reverse fraudulent charges, and protect your finances.
3. Notify Local Law Enforcement
File a report with your local police department. While they may not be able to investigate every case, having a report on file is often helpful for other steps you may need to take.
We are actively reporting this fraud to Meta (Facebook & Instagram) and hope to have the scam pages and ads removed as soon as possible, but in the meantime, your vigilance is the strongest defense.
Informational Videos
Dangers of Public Wi-Fi:
Security Dangers of Public Wi-Fi – by Kaspersky
Beware free Wi-Fi may not be as free as we think – Report by CBS Boston:
StaySafeOnline.org – Security Awareness Series
Linked Resources
America’s Cyber Defense Agency Report an Incident | CISA
Everything you need to know about Social Security related scams, including a place to report potential Social Security related scams: https://www.ssa.gov/scam/
Stay safe online.
The National Cybersecurity Alliance provides a collection of digital resources, at your virtual fingertips. They want to make it easy for everyone to learn more about cybersecurity and staying safe online. That’s why they collected all of these easy-to-follow resources and guides to share with you: Resources + Guides – National Cybersecurity Alliance (staysafeonline.org)
Staying Safe Online: Staying safe online | ICPEN

FCC Internet Safety Tips: Internet Safety Tips (fcc.gov)

The FBI and how they can help you regarding scams: On the Internet: Be Cautious When Connected — FBI
Recommended Downloads
Protect Your Digital Life – Password Management for Individuals and Families: https://bitwarden.com/products/personal/
Common Threats and How to Spot them
Top 15 Types of Cybersecurity Risks & How To Prevent Them
Understanding the Types of Cyber Threats
There’s no getting around the fact that cybersecurity is a real problem facing anyone with a device. Individual, business, organization, it doesn’t matter. With the widespread use of technology and its reliance on connectivity, it’s a prime market for malware. Since the inception of the internet, all sorts of security risks have come and gone. Their severity ranges from a minor nuisance to devastating, and you can be sure malicious attacks will remain so long as the net does.
But, as scary as it sounds, there are plenty of common types of security risks which are both identifiable and preventable. In this article, we’re going to put the magnifying glass on the types of security risks and attacks facing people today, along with methods to stop them.
15 Common Cybersecurity Risks
1 – Malware
We’ll start with the most prolific and common form of security threat: malware. It’s been around since the internet’s inception and continues to remain a consistent problem. Malware is when an unwanted piece of programming or software installs itself on a target system, causing unusual behavior. This ranges from denying access to programs, deleting files, stealing information, and spreading itself to other systems.
Prevention: A proactive approach is the best defense. Common sense dictates users and organizations should have the latest anti-malware programs installed, for starters. It’s also important to recognize suspicious links, files, or websites, which are effective ways of implementing malware. Often, a combination of caution and anti-virus is enough to thwart most malware concerns.
2 – Password Theft
“I’ve been hacked!” A common conclusion when you log in to an account, only to find your password changed and details lost. The reality is an unwanted third party managed to steal or guess your password and has since run amok with the information. It’s far worse for an enterprise, which may lose sensitive data.
Prevention: There are several reasons for losing a password. Attackers may guess the password or use “brute force” programs to cycle through thousands of potential attempts. They may also steal it from an unsafe location or use social engineering to trick a user into giving it away. Two-factor authentication is a robust protection method, as it requires an additional device to complete the login. Additionally, using complicated logins thwarts brute force attempts.
3 – Traffic Interception
Also known as “eavesdropping,” traffic interception occurs when a third-party “listens” to info sent between a user and host. The kind of information stolen varies based on traffic but is often used to take log-ins or valuable data.
Prevention: Avoiding compromised websites (such as those not using HTML5) is an excellent proactive defense. Encrypting network traffic – such as through a VPN – is another preventive method.
4 – Phishing Attacks
Phishing scams are an older attack method and rely on social engineering to achieve its goal. Typically, an end user receives a message or email which requests sensitive data, such as a password. Sometimes, the phishing message appears official, using legitimate appearing addresses and media. This compels an individual to click on links and accidentally give away sensitive information.
Prevention: Generally, a common-sense approach to security is the best prevention. Phishing messages are often rife with spelling and syntax errors. Official emails from organizations do not request personal data, so this is a giveaway there is malicious intent.
5 – DDoS
Distributed Denial of Service is an attack method in which malicious parties target servers an overload them with user traffic. When a server cannot handle incoming requests, the website it hosts shuts down or slows to unusable performance.
Prevention: Stopping a DDoS requires identifying malicious traffic and halting access. This can take time depending on how many malicious IP’s are used to distribute the attack. In most cases, servers need to be taken offline for maintenance.
6 – Cross Site Attack
Referred to as an XSS attack. In this instance, a third-party will target a vulnerable website, typically one lacking encryption. Once targeted the dangerous code loads onto the site. When a regular user accesses said website, that payload is delivered either to their system or browser, causing unwanted behavior. The goal is to either disrupt standard services or steal user information.
Prevention: Encryption is usually required on the host’s side. Additionally, providing the option to turn off page scripts is vital to thwart a malicious payload from activating. Users can also install script-blocker add-ons to their browser if they prefer additional browsing control.
7 – Zero-Day Exploits
Occurring after the discovery of a “zero-day vulnerability,” an exploit is a targeted attack against a system, network, or software. This attack takes advantage of an overlooked security problem, looking to cause unusual behavior, damage data, and steal information.
Prevention: Stopping exploits is challenging, as it relies on the vendor both discovering the loophole and releasing a fix for it. In some cases, a zero-day vulnerability can exist for an extended period before its discovered. Users must maintain good safety habits until a fix is released.
8 – SQL Injection
An SQL attack is essentially data manipulation, implemented to access information which isn’t meant to be available. Essentially, malicious third parties manipulate SQL “queries” (the typical string of code request sent to a service or server) to retrieve sensitive info.
Prevention: Implementation of smart firewalls is one prevention method; application firewalls can detect and filter out unwanted requests. Generally, the most effective way is to develop code which identifies illegal user inputs.
9 – Social Engineering
Similar to phishing, social engineering is the umbrella method for attempting to deceive users into giving away sensitive details. This can occur on any platform, and malicious parties will often go to great lengths to accomplish their goals, such as utilizing social-media info.
Prevention: Remaining skeptical of suspicious messages, friend requests, emails, or attempts to collect user info from unknown third-parties.
10 – MitM Attack
A Man-in-the-Middle attack occurs when a third-party hijacks a session between client and host. The hacker generally cloaks itself with a spoofed IP address, disconnects the client, and requests information from the client. For example, attempting to log-in to a bank session would allow a MITM attack to hijack user info related to their bank account.
Prevention: Encryption and use of HTML5 are recommended.
11 – Ransomware
A nasty variant of malware, ransomware installs itself on a user system or network. Once installed, it prevents access to functionalities (in part or whole) until a “ransom” is paid to third parties.
Prevention: Removal is challenging once installed. Keeping anti-virus updated and avoiding malicious links are the best current prevention methods. Also, current backups and replications are key to keeping ransomware attacks from becoming catastrophic.
12 – Cryptojacking
Cryptojacking is an attempt to install malware which forces the infected system to perform “crypto-mining,” a popular form of gaining crypto-currency. This, like other viruses, can infect unprotected systems. It is deployed because the act of crypto-mining is hardware intensive.
Prevention: Keep all security apps/software updated and make sure firmware on smart devices is also using the latest version. Cryptojacking can infect most unprotected systems.
13 – Water Hole Attack
Generally used to target organizations, water hole attacks occur when a group infects websites a particular organization frequently uses. The goal – much like a cross-site attack – is to load a malicious payload from the infected sites.
Prevention: Anti-virus can passively identify dangerous scripts. Keep website scripts off as a default if your enterprise suspects an infection.
14 – Drive-By Attack
In a drive-by-attack, malicious code is delivered onto a system or device. The distinction, however, is that no action is needed on the user end, where typically they need to click a link or download an executable.
Prevention: Avoid suspicious websites. Normally, compromised websites are flagged by search engines and anti-malware programs.
15 – Trojan Virus
Trojan malware attempts to deliver its payload by disguising itself as legitimate software. One technique used was an “alert” a user’s system was compromised by malware, recommending a scan, whereby the scan actually delivered the malware.
Prevention: Avoid downloading programs or executable from unrecognized vendors or those that attempt to alarm the user to a serious problem.
Conclusion
These types of cyber risks continue to grow in complexity, but understanding them is the best way to better defend your networks and systems.
https://www.executech.com/insights/top-15-types-of-cybersecurity-attacks-how-to-prevent-them/
Staying safe with Social Media
There are lots of ways to protect your personal information and data from scammers. But what happens if your email or social media account gets hacked? Here are some quick steps to help you recover your email or social media account.
Signs That Someone Hacked Your Account
Hackers try to take over your accounts. Some might want to steal your personal information — like your usernames and passwords, bank account numbers, or Social Security number — to commit identity theft. Others might want to spread malware or scam others. So, what types of things might tip you off that someone hacked your account and changed your password?
- You can’t log in to your account.
- You get a notification about a change to your username or password— but you didn’t make that change.
- You get a notification that someone logged into your account from a device you don’t recognize or a location you’re not at.
- Your friends or family report getting emails or messages you didn’t send, sometimes with random links or fake pleas for help or money.
How To Get Back Into Your Hacked Account
First, make sure your computer security software is up to date, then run a scan. If the scan identifies suspicious software, delete it, and restart your computer. Then, follow the provider’s account recovery instructions.
|
Email Account Recovery Links |
Social Media Account Recovery Links |
What To Do After You Take Back Control of Your Hacked Account
After you get back into your hacked account
- take steps to secure your account
- check for signs that someone had access to your account
- notify your contacts about the hack
Take steps to secure your account
- Change your account password. Create a strong password that is hard to guess.
- Sign out of all devices. That way anyone who’s logged in to your account on another device will get kicked out.
- Turn on two-factor authentication (2FA), also known as two-step verification, if it’s available on your accounts. With 2FA, you’ll have to enter your password and something else to log in. That could be a PIN or a one-time verification code you get by text or email or from an authenticator app.
- Check your account recovery information. Make sure the recovery email addresses and phone numbers listed are ones you entered and have access to.
Check for signs that someone had access to your account
- Check your email settings to see if there are rules set up to forward emails. Delete any rules you didn’t set up, so your messages aren’t forwarded to someone else’s address.
- Check your sent folder for emails the hacker sent from your account. Look in your deleted folder for emails the hacker may have read then deleted.
- Check your social media accounts for messages the hacker posted or sent from your account, or for new friends you don’t recognize.
Tell your contacts
Send your friends a quick email or text, or post something, to let them know about the hack. Tell them not to click on links in emails from you and to ignore pleas for help or money.
Why It’s So Important To Protect Your Email Account
Your email account is an important part of protecting your personal information online. Why? Say you forget your account password and use the password reset feature to get a new one. You get an email with a password reset link, click on it, and change your account password. All in a matter of minutes.
Now, imagine if someone hacked your email account. They could request a password reset link for any of your other accounts, get the password reset link from your inbox, change your password, and lock you out of the account.
That’s why it’s critical to protect your email account by using a strong password and turning on two-factor authentication.
How To Recover Your Hacked Email or Social Media Account | Consumer Advice (ftc.gov)
Do you think your data has been compromised?
10 COMMON STEPS TO TAKE AFTER YOUR PERSONAL DATA IS COMPROMISED ONLINE
Unfortunately, data breaches have become a common feature of modern life in our always-connected world of online services; everyone in the U.S. is at risk of having their data stolen. However, even if your data is compromised in a data breach, you don’t have to become a victim. There are several steps you can take to contain the damage and keep your personal finances, credit score, and identity safe from criminals.
If you find out that a company you do business with – or an online service that you use – has suffered a data breach, here are some steps to take right away:
1. Change your passwords
It’s a good idea to keep changing your password on a regular basis, but in the aftermath of a data breach, it’s especially important to change your passwords to something strong, secure, and unique. And you should have multiple “passwords,” not just one. Do not use the same password for all your online accounts. In general, a “strong” password is at least 8 characters with a mixture of letters, numbers, and symbols. Consider using a password manager to help generate and keep track of your passwords.
2. Force a logout of any active sessions
Sometimes an attacker may currently have access to your account and some services offer the ability to check recent activity or view current logins. It is best practice to initiate a logout of any currently logged in sessions to prevent unauthorized users from remaining in your account. This will make it very difficult for them to get back in since you changed your password.
3. Sign up for two-factor authentication
In addition to changing your passwords, sign up for two-factor authentication (also known as “2FA” or “two-step verification”) wherever possible. This is an added layer of security for your account logins, and many services such as Gmail and Facebook now offer it. With two-factor authentication, your online account will require you to enter an additional level of identification to access your account – such as a code sent to your phone. This means that even if hackers get your email and password, they can’t get into your account without that second factor of identity verification. Also verify the information is correct such as email address and phone number.
4. Check for updates from the company and official news agencies
If your data is involved in a major data breach, the company will likely post ongoing updates and disclosures about which customers were affected. For example, after a recent Facebook data breach, the company automatically logged out the users whose accounts were affected and sent them messages via the platform about what had happened and what to do next. After the Equifax data breach, the Federal Trade Commission (FTC) offered a series of advisories and steps that people could take to protect themselves.
5. Check for security updates for apps and devices
Updating your apps to the latest version gives you access to the latest features and improves app security and stability. It’s not just apps, though. Operating system updates are important as well. Why
do Apple, Android, and Microsoft do updates? Things change quickly in tech. You can’t wait for a new phone to release new features and new security, so it is released in as real time as possible. This also helps you learn a couple of new features at a time, rather than being overwhelmed by a big change. As with apps, security patches are a big part of OS updates – it helps keep you secure and protects against viruses.
6. Watch your accounts, check your credit reports
After a data breach, it’s essential to be vigilant and pay extra attention to your account activity – that includes your account at the company that suffered the breach, as well as your bank account and other financial accounts. Read your credit card statements and watch for suspicious transactions. Also, sign up for your free annual credit report to check your credit reports from each of the three credit reporting bureaus.
7. Stay Aware
Be aware of suspicious text messages, emails, or phone calls – never give out any financial, personal, or confidential information and contact law enforcement if you believe that someone has access to your personal information. Do not click links in emails or text messages unless you can verify them with undoubted certainty – it is best to type the link to a known website manually.
8. Consider identity theft protection services
If you want additional peace of mind, you can consider signing up for identity theft protection services. However, these services are not cheap, and you can do many of the actions yourself. Often when there is a significant data breach, the company involved will give affected customers a free year of credit monitoring.
9. Freeze your credit
Another step you can take, whether you’re affected by a data breach or not, is to freeze your credit. You can do this by contacting each of the three credit bureaus (Equifax, Experian, and TransUnion) and asking to freeze your credit. There is no cost to freeze your credit, and it will prevent any new credit accounts from being opened in your name. Even if identity thieves have access to all your personal data, they can’t open new accounts under your name if your credit is frozen. The only drawback of freezing your credit is that it prevents you from applying for new credit too – so don’t do it if you are expecting to need a new car loan, home loan, or credit card account. You can un-freeze your credit at any time.
10. Go to IdentityTheft.gov
If you are affected by a data breach, there is a government website that can help you assess the situation and understand your options for what to do next. There are a variety of resources with tips and advice on what to do if your personal information was lost or stolen.
Being affected by a data breach can be alarming, and in the worst-case scenario, it can lead to identity theft and financial complications. But if you know what to expect, and you take a few simple steps to protect yourself and stay vigilant, you can overcome the risks and hassles of a data breach.
Forum
Private








